
In 2015, researchers reported a surprising discovery that stoked industry-wide security concerns—an attack called RowHammer that could corrupt, modify, or steal sensitive data when a simple user-level application repeatedly accessed certain regions of DDR memory chips. In the coming years, memory chipmakers scrambled to develop defenses that prevented the attack, mainly by limiting the number of times programs could open and close the targeted chip regions in a given time.
Recently, researchers devised a new method for creating the same types of RowHammer-induced bitflips even on a newer generation of chips, known as DDR4, that have the RowHammer mitigations built into them. Known as RowPress, the new attack works not by “hammering” carefully selected regions repeatedly, but instead by leaving them open for longer periods than normal. Bitflips refer to the phenomenon of bits represented as ones change to zeros and vice versa.
Further amplifying the vulnerability of DDR4 chips to read-disturbance attacks—the generic term for inducing bitflips through abnormal accesses to memory chips—RowPress bitflips can be enhanced by combining them with RowHammer accesses. Curiously, raising the temperature of the chip also intensifies the effect.
“We demonstrate a proof of concept RowPress program that can cause bitflips in a real system that already employs protections against RowHammer,” Onur Mutlu, a professor at ETH Zürich and a co-author of a recently published paper titled RowPress: Amplifying Read Disturbance in Modern DRAM Chips, wrote in an email. “Note that this is not in itself an attack. It simply shows that bitflips are possible and plenty, which can easily form the basis of an attack. As many prior works in security have shown, once you can induce a bitflip, you can use that bitflip for various attacks.”
DIMMs, bits, and cosmic rays
The basic building block of DRAM (dynamic random access memory) is a storage cell. Each cell comprises a capacitor and a transistor and stores a single bit of data. When a bit is put into a memory cell, the transistor is used to charge or discharge the capacitor. A charged capacitor is represented with a 1, while a discharged capacitor is represented with a 0. Most often, DRAM cells are organized into a rectangular array of rows and columns.
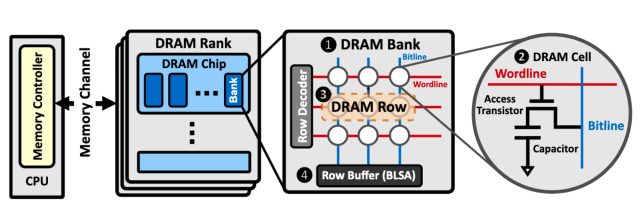
These rows and columns are arranged into ranks and banks to form what’s known as the dual in-line memory module. Better known as a DIMM, this rectangular stick plugs into the computer motherboard. When a computer accesses a chunk of memory, it opens the rows to the cells storing the desired data and transfers it to the CPU.
Bitflips have long been known as a rare, naturally occurring phenomenon. They occur when an unexpected flow of electrons within a transistor’s gates changes the voltage between the source, or the part of the circuit where flow originates, and the sink, where the flow is received. During a 2003 election in Belgium, cosmic rays from outer space are widely believed to have caused bitflips that gave a political candidate an additional 4,096 votes before being corrected. (The number 4,096, which can also be expressed as 212, suggests there was a bitflip in the 12th bit.)
Then, in 2014, discovered a previously unknown way to artificially induce bitflips at will. When a computer repeatedly hammered a DRAM row, they found they could induce bitflips in adjacent rows. In RowHammer parlance, the row that gets hammered is known as the aggressor row. The row where bits are flipped is known as the victim row.

